Table of Contents
Early releases of Samba-3 implemented new capability to work concurrently with multiple account backends. This capability was removed beginning with release of Samba 3.0.23. Commencing with Samba 3.0.23 it is possible to work with only one specified passwd backend.
The three passdb backends that are fully maintained (actively supported) by the Samba Team are: smbpasswd (being obsoleted), tdbsam (a tdb-based binary file format), and ldapsam (LDAP directory). Of these, only the ldapsam backend stores both POSIX (UNIX) and Samba user and group account information in a single repository. The smbpasswd and tdbsam backends store only Samba user accounts.
In a strict sense, there are three supported account storage and access systems. One of these is considered obsolete (smbpasswd). It is recommended to use the tdbsam method for all simple systems. Use ldapsam for larger and more complex networks.
In a strict and literal sense, the passdb backends are account storage mechanisms (or methods) alone. The choice of terminology can be misleading, however we are stuck with this choice of wording. This chapter documents the nature of the account storage system with a focus on user and trust accounts. Trust accounts have two forms, machine trust accounts (computer accounts) and interdomain trust accounts. These are all treated as user-like entities.
Samba-3 provides for complete backward compatibility with Samba-2.2.x functionality as follows:
This isn't really a backend at all, but is listed here for simplicity. Samba can be configured to pass plaintext authentication requests to the traditional UNIX/Linux /etc/passwd and /etc/shadow -style subsystems. On systems that have Pluggable Authentication Modules (PAM) support, all PAM modules are supported. The behavior is just as it was with Samba-2.2.x, and the protocol limitations imposed by MS Windows clients apply likewise. Please refer to Technical Information, for more information regarding the limitations of plaintext password usage.
This option allows continued use of the smbpasswd file that maintains a plain ASCII (text) layout that includes the MS Windows LanMan and NT-encrypted passwords as well as a field that stores some account information. This form of password backend does not store any of the MS Windows NT/200x SAM (Security Account Manager) information required to provide the extended controls that are needed for more comprehensive interoperation with MS Windows NT4/200x servers.
This backend should be used only for backward compatibility with older versions of Samba. It may be deprecated in future releases.
ldapsam_compat (Samba-2.2 LDAP Compatibility)
There is a password backend option that allows continued operation with an existing OpenLDAP backend that uses the Samba-2.2.x LDAP schema extension. This option is provided primarily as a migration tool, although there is no reason to force migration at this time. This tool will eventually be deprecated.
Samba-3 introduces a number of new password backend capabilities.
This backend provides a rich database backend for local servers. This backend is not suitable for multiple domain controllers (i.e., PDC + one or more BDC) installations.
The tdbsam password backend stores the old smbpasswd information plus the extended MS Windows NT/200x SAM information into a binary format TDB (trivial database) file. The inclusion of the extended information makes it possible for Samba-3 to implement the same account and system access controls that are possible with MS Windows NT4/200x-based systems.
The inclusion of the tdbsam capability is a direct response to user requests to allow simple site operation without the overhead of the complexities of running OpenLDAP. It is recommended to use this only for sites that have fewer than 250 users. For larger sites or implementations, the use of OpenLDAP or of Active Directory integration is strongly recommended.
This provides a rich directory backend for distributed account installation.
Samba-3 has a new and extended LDAP implementation that requires configuration of OpenLDAP with a new format Samba schema. The new format schema file is included in the examples/LDAP directory of the Samba distribution.
The new LDAP implementation significantly expands the control abilities that were possible with prior versions of Samba. It is now possible to specify “ per-user ” profile settings, home directories, account access controls, and much more. Corporate sites will see that the Samba Team has listened to their requests both for capability and greater scalability.
Old Windows clients send plaintext passwords over the wire. Samba can check these passwords by encrypting them and comparing them to the hash stored in the UNIX user database.
Newer Windows clients send encrypted passwords (LanMan and NT hashes) instead of plaintext passwords over the wire. The newest clients will send only encrypted passwords and refuse to send plaintext passwords unless their registry is tweaked.
Many people ask why Samba cannot simply use the UNIX password database. Windows requires passwords that are encrypted in its own format. The UNIX passwords can't be converted to Windows-style encrypted passwords. Because of that, you can't use the standard UNIX user database, and you have to store the LanMan and NT hashes somewhere else.
In addition to differently encrypted passwords, Windows also stores certain data for each user that is not stored in a UNIX user database: for example, workstations the user may logon from, the location where the user's profile is stored, and so on. Samba retrieves and stores this information using a passdb backend. Commonly available backends are LDAP, tdbsam, and plain text file. For more information, see the man page for smb.conf regarding the passdb backend parameter.
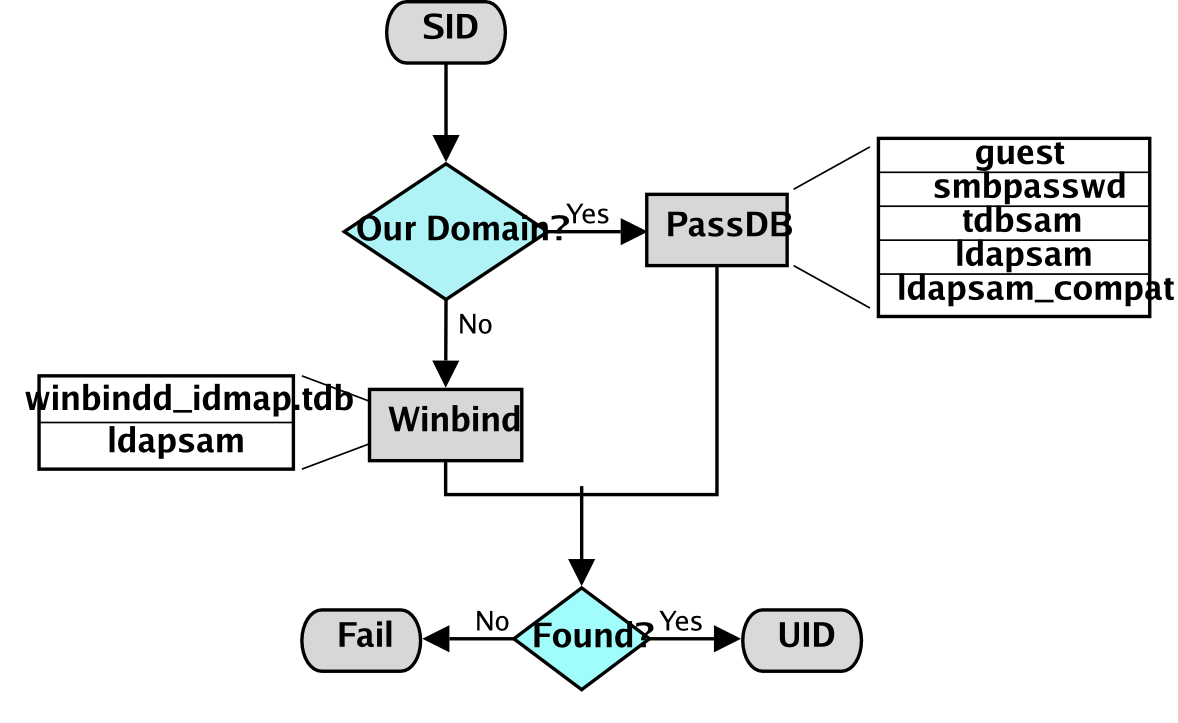
Figure�11.1.�IDMAP: Resolution of SIDs to UIDs.

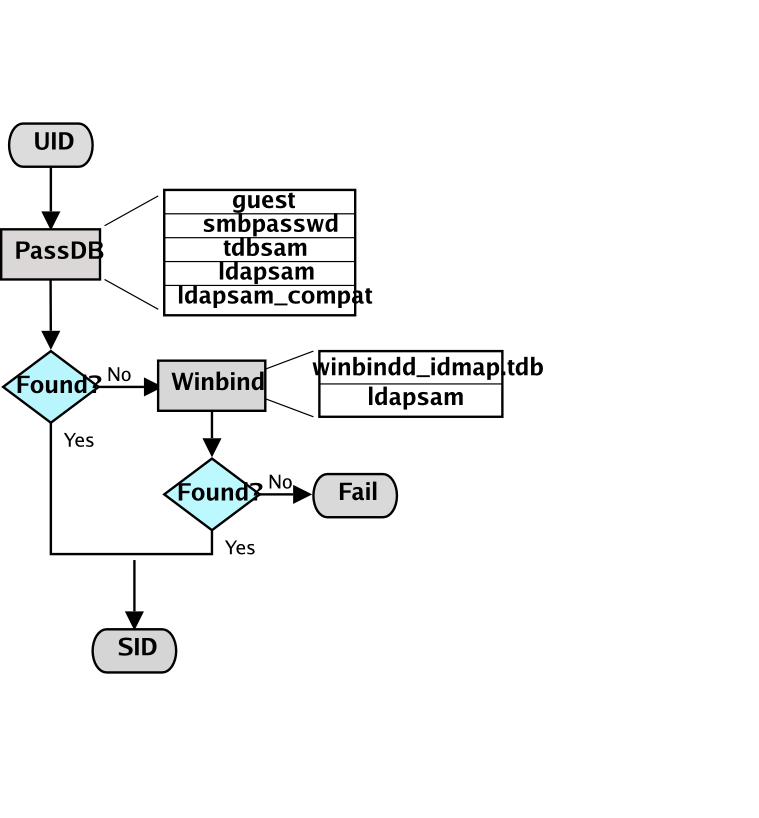
The resolution of SIDs to UIDs is fundamental to correct operation of Samba. In both cases shown, if winbindd is not running or cannot be contacted, then only local SID/UID resolution is possible. See resolution of SIDs to UIDs and resolution of UIDs to SIDs diagrams.
Figure�11.2.�IDMAP: Resolution of UIDs to SIDs.
The UNIX and SMB password encryption techniques seem similar on the surface. This similarity is, however, only skin deep. The UNIX scheme typically sends clear-text passwords over the network when logging in. This is bad. The SMB encryption scheme never sends the clear-text password over the network, but it does store the 16-byte hashed values on disk. This is also bad. Why? Because the 16 byte hashed values are a “ password equivalent. ” You cannot derive the user's password from them, but they could potentially be used in a modified client to gain access to a server. This would require considerable technical knowledge on behalf of the attacker but is perfectly possible. You should therefore treat the data stored in whatever passdb backend you use (smbpasswd file, LDAP) as though it contained the clear-text passwords of all your users. Its contents must be kept secret, and the file should be protected accordingly.
Ideally, we would like a password scheme that involves neither plaintext passwords on the network nor plaintext passwords on disk. Unfortunately, this is not available because Samba is stuck with having to be compatible with other SMB systems (Windows NT, Windows for Workgroups, Windows 9x/Me).
Windows NT 4.0 Service Pack 3 changed the default setting so plaintext passwords are disabled from being sent over the wire. This mandates either the use of encrypted password support or editing the Windows NT registry to re-enable plaintext passwords.
The following versions of Microsoft Windows do not support full domain security protocols, although they may log onto a domain environment:
MS Windows XP Home does not have facilities to become a domain member, and it cannot participate in domain logons.
The following versions of MS Windows fully support domain security protocols.
All current releases of Microsoft SMB/CIFS clients support authentication via the SMB challenge/response mechanism described here. Enabling clear-text authentication does not disable the ability of the client to participate in encrypted authentication. Instead, it allows the client to negotiate either plaintext or encrypted password handling.
MS Windows clients will cache the encrypted password alone. Where plaintext passwords are re-enabled through the appropriate registry change, the plaintext password is never cached. This means that in the event that a network connections should become disconnected (broken), only the cached (encrypted) password will be sent to the resource server to effect an auto-reconnect. If the resource server does not support encrypted passwords, the auto-reconnect will fail. Use of encrypted passwords is strongly advised.
Every operation in UNIX/Linux requires a user identifier (UID), just as in MS Windows NT4/200x this requires a security identifier (SID). Samba provides two means for mapping an MS Windows user to a UNIX/Linux UID.
First, all Samba SAM database accounts require a UNIX/Linux UID that the account will map to. As users are added to the account information database, Samba will call the add user script interface to add the account to the Samba host OS. In essence all accounts in the local SAM require a local user account.
The second way to map Windows SID to UNIX UID is via the idmap uid and idmap gid parameters in smb.conf . Please refer to the man page for information about these parameters. These parameters are essential when mapping users from a remote (non-member Windows client or a member of a foreign domain) SAM server.
Samba-3 has a special facility that makes it possible to maintain identical UIDs and GIDs on all servers in a distributed network. A distributed network is one where there exists a PDC, one or more BDCs, and/or one or more domain member servers. Why is this important? This is important if files are being shared over more than one protocol (e.g., NFS) and where users are copying files across UNIX/Linux systems using tools such as rsync .
The special facility is enabled using a parameter called idmap backend . The default setting for this parameter is an empty string. Technically it is possible to use an LDAP-based idmap backend for UIDs and GIDs, but it makes most sense when this is done for network configurations that also use LDAP for the SAM backend. Example Configuration with the LDAP idmap Backend shows that configuration.
Example�11.1.�Example Configuration with the LDAP idmap Backend
| [global] |
| idmap backend = ldap:ldap://ldap-server.quenya.org:636 |
| # Alternatively, this could be specified as: |
| idmap backend = ldap:ldaps://ldap-server.quenya.org |
A network administrator who wants to make significant use of LDAP backends will sooner or later be exposed to the excellent work done by PADL Software. PADL http://www.padl.com have produced and released to open source an array of tools that might be of interest. These tools include:
There is much excitement and interest in LDAP directories in the information technology world today. The LDAP architecture was designed to be highly scalable. It was also designed for use across a huge number of potential areas of application encompassing a wide range of operating systems and platforms. LDAP technologies are at the heart of the current generations of Federated Identity Management (FIM) solutions that can underlie a corporate Single Sign-On (SSO) environment.
LDAP implementations have been built across a wide variety of platforms. It lies at the core of Microsoft Windows Active Directory services (ADS), Novell's eDirectory, as well as many others. Implementation of the directory services LDAP involves interaction with legacy as well as new generation applications, all of which depend on some form of authentication services.
UNIX services can utilize LDAP directory information for authentication and access controls through intermediate tools and utilities. The total environment that consists of the LDAP directory and the middle-ware tools and utilities makes it possible for all user access to the UNIX platform to be managed from a central environment and yet distributed to wherever the point of need may be physically located. Applications that benefit from this infrastructure include: UNIX login shells, mail and messaging systems, quota controls, printing systems, DNS servers, DHCP servers, and also Samba.
Many sites are installing LDAP for the first time in order to provide a scalable passdb backend for Samba. Others are faced with the need to adapt an existing LDAP directory to new uses such as for the Samba SAM backend. Whatever your particular need and attraction to Samba may be, decisions made in respect of the design of the LDAP directory structure and its implementation are of a durable nature for the site. These have far-reaching implications that affect long-term information systems management costs.
Do not rush into an LDAP deployment. Take the time to understand how the design of the Directory Information Tree (DIT) may impact current and future site needs, as well as the ability to meet them. The way that Samba SAM information should be stored within the DIT varies from site to site and with each implementation new experience is gained. It is well understood by LDAP veterans that first implementations create awakening, second implementations of LDAP create fear, and third-generation deployments bring peace and tranquility.
Samba requires UNIX POSIX identity information as well as a place to store information that is specific to Samba and the Windows networking environment. The most used information that must be dealt with includes: user accounts, group accounts, machine trust accounts, interdomain trust accounts, and intermediate information specific to Samba internals.
The example deployment guidelines in this book, as well as other books and HOWTO documents available from the internet may not fit with established directory designs and implementations. The existing DIT may not be able to accommodate the simple information layout proposed in common sources. Additionally, you may find that the common scripts and tools that are used to provision the LDAP directory for use with Samba may not suit your needs.
It is not uncommon, for sites that have existing LDAP DITs to find necessity to generate a set of site-specific scripts and utilities to make it possible to deploy Samba within the scope of site operations. The way that user and group accounts are distributed throughout the DIT may make this a challenging matter. The solution will, of course, be rewarding, but the journey to it may be challenging. Take time to understand site needs and do not rush into deployment.
Above all, do not blindly use scripts and tools that are not suitable for your site. Check and validate all scripts before you execute them to make sure that the existing infrastructure will not be damaged by inadvertent use of an inappropriate tool.
Samba doesn't provide a turnkey solution to LDAP. It is best to deal with the design and configuration of an LDAP directory prior to integration with Samba. A working knowledge of LDAP makes Samba integration easy, and the lack of a working knowledge of LDAP can make it a frustrating experience.
Computer (machine) accounts can be placed wherever you like in an LDAP directory subject to some constraints that are described in this chapter.
The POSIX and sambaSamAccount components of computer (machine) accounts are both used by Samba. Thus, machine accounts are treated inside Samba in the same way that Windows NT4/200X treats them. A user account and a machine account are indistinguishable from each other, except that the machine account ends in a $ character, as do trust accounts.
The need for Windows user, group, machine, trust, and other accounts to be tied to a valid UNIX UID is a design decision that was made a long way back in the history of Samba development. It is unlikely that this decision will be reversed or changed during the remaining life of the Samba-3.x series.
The resolution of a UID from the Windows SID is achieved within Samba through a mechanism that must refer back to the host operating system on which Samba is running. The NSS is the preferred mechanism that shields applications (like Samba) from the need to know everything about every host OS it runs on.
Samba asks the host OS to provide a UID via the “ passwd ”, “ shadow ”, and “ group ” facilities in the NSS control (configuration) file. The best tool for achieving this is left up to the UNIX administrator to determine. It is not imposed by Samba. Samba provides winbindd with its support libraries as one method. It is possible to do this via LDAP, and for that Samba provides the appropriate hooks so that all account entities can be located in an LDAP directory.
For many the weapon of choice is to use the PADL nss_ldap utility. This utility must be configured so that computer accounts can be resolved to a POSIX/UNIX account UID. That is fundamentally an LDAP design question. The information provided on the Samba list and in the documentation is directed at providing working examples only. The design of an LDAP directory is a complex subject that is beyond the scope of this documentation.
Samba provides two tools for management of user and machine accounts: smbpasswd and pdbedit .
The pdbedit can be used to manage account policies in addition to Samba user account information. The policy management capability is used to administer domain default settings for password aging and management controls to handle failed login attempts.
Some people are confused when reference is made to smbpasswd because the name refers to a storage mechanism for SambaSAMAccount information, but it is also the name of a utility tool. That tool is destined to eventually be replaced by new functionality that is being added to the net toolset (see the Net Command).
The smbpasswd utility is similar to the passwd and yppasswd programs. It maintains the two 32 byte password fields in the passdb backend. This utility operates independently of the actual account and password storage methods used (as specified by the passdb backend in the smb.conf file).
smbpasswd works in a client-server mode where it contacts the local smbd to change the user's password on its behalf. This has enormous benefits.
smbpasswd has the capability to change passwords on Windows NT servers (this only works when the request is sent to the NT PDC if changing an NT domain user's password).
smbpasswd can be used to:
To run smbpasswd as a normal user, just type:
$smbpasswdOld SMB password:secret
For secret , type the old value here or press return if there is no old password.
New SMB Password:new secretRepeat New SMB Password:new secret
If the old value does not match the current value stored for that user, or the two new values do not match each other, then the password will not be changed.
When invoked by an ordinary user, the command will allow only the user to change his or her own SMB password.
When run by root, smbpasswd may take an optional argument specifying the username whose SMB password you wish to change. When run as root, smbpasswd does not prompt for or check the old password value, thus allowing root to set passwords for users who have forgotten their passwords.
smbpasswd is designed to work in the way familiar to UNIX users who use the passwd or yppasswd commands. While designed for administrative use, this tool provides essential user-level password change capabilities.
For more details on using smbpasswd , refer to the man page (the definitive reference).
pdbedit is a tool that can be used only by root. It is used to manage the passdb backend, as well as domain-wide account policy settings. pdbedit can be used to:
Under the terms of the Sarbanes-Oxley Act of 2002, American businesses and organizations are mandated to implement a series of internal controls and procedures to communicate, store, and protect financial data. The Sarbanes-Oxley Act has far reaching implications in respect of:
In short, the Sarbanes-Oxley Act of 2002 is an instrument that enforces accountability in respect of business related information systems so as to ensure the compliance of all information systems that are used to store personal information and particularly for financial records processing. Similar accountabilities are being demanded around the world.
The need to be familiar with the Samba tools and facilities that permit information systems operation in compliance with government laws and regulations is clear to all. The pdbedit is currently the only Samba tool that provides the capacity to manage account and systems access controls and policies. During the remaining life-cycle of the Samba-3 series it is possible the new tools may be implemented to aid in this important area.
Domain global policy controls available in Windows NT4 compared with Samba is shown in NT4 Domain v's Samba Policy Controls.
Table�11.1.�NT4 Domain v's Samba Policy Controls